|
Overview
Organizations invest millions of dollars and tremendous effort in their IdM implementations, hoping to gain better security, higher productivity and quick ROI. However, it is very difficult to attain these goals without improving the current quality of privileges, and without creating a privileges model that reflects well the underlying business.
A role-based approach to privileges management is widely considered as best practice in the deployment of an effective provisioning system. Most organizations believe that Role-based Access Control (RBAC) is necessary to unlock the full benefits of Identity Management, and that without this change in paradigm the existing mess will prevail and in fact will be amplified by the new privileges automation systems. Yet, 81% of IdM project managers find that existing IdM solutions do not provide adequate tools for the creation and ongoing management of a role-based privileges model.
Eurekify provides an integrated approach to ERM, complementing and empowering any existing IdM solution with these new and powerful capabilities. Eurekify Sage ERM is the only solution that provides for the full lifecycle of Enterprise Role Management, making many of the difficult processes feasible through the assistance of unique and patented analytics. Eurekify Sage ERM reflects business needs and ongoing changes into IdM provisioning policies and processes.
The Need
The Eurekify Role-based IdM solution is intended for organizations that are before, during, or after the initial deployment of an Identity Management Provisioning system:
- Enterprises intending to deploy Identity Management Provisioning solutions need to
- gain a better understanding of their own IdM needs, in order to better evaluate alternative solutions and prioritize systems for IdM deployment
- gain control over the current quality of privileges, and if necessary start a preparatory cleanup project
- demonstrate a clear contribution of the IdM effort to the organizational compliance requirements
- Enterprises currently deploying an automated provisioning system need to
- identify key provisioning policies and roles for automation
- cleanup and rearrange some systems
- Enterprises that have already deployed an automated provisioning system may need to
- create and maintain a role-based model to align provisioning policies with business roles
- analyze new systems and applications before they are loaded into the IdM system
- automate verification of IT controls and compliance with regulatory requirements
- Enterprises in all IdM phases usually have some compliance needs that can be addressed with an effective role management system
Key Deliverables
Eurekify Sage ERM for Role-based Identity Management can be deployed in conjunction with the Identity Management systems of virtually all vendors, and even with home grown systems, delivering:
- Preliminary pre-IdM assessment of target systems, including a review of alternative role management approaches
- Creation of a role-based privileges model to be used as a reference and to be uploaded into the provisioning system for ongoing operational use
- Ongoing maintenance of the role-based privileges model, and periodical synchronization with the provisioning system
- Automated verification of IT Controls and compliance with SoD and other business process rules
- Automated detection of exceptions and deviations, and other privileges cleanup functions
- Automated certification of roles and individual privileges by business managers
- Periodical management reporting on privileges quality, privileges management, and compliance processes
How it Works:
Eurekify’s phased approach to deploying Role-based Identity Management relies on the 5C’s of Enterprise Role Management – Control, Create, Comply, Correlate and Collaborate. The following diagram describes how organizations can achieve a successful deployment of Role-based IdM, and realize the full benefits of IdM with Eurekify Sage ERM.
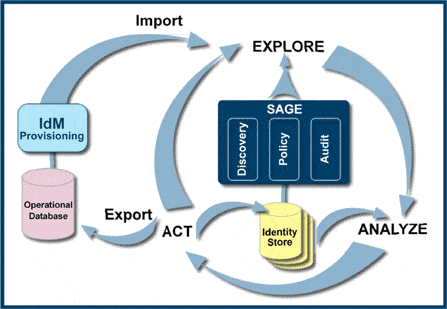
Role Management in Support of Identity Management
The “Survey, Plan, Deploy and Manage” methodology guides organizations through the phases of surveying their current state, preparing for the IdM implementation, implementing role-based IdM and managing the IdM framework.
This methodology is offered by Eurekify partners worldwide. It is applicable to any Identity Management and Provisioning system of choice, including but not limited to IBM Tivoli, HP, Sun, BMC, CA, Microsoft, and Thor/Oracle.


- Analyze privileges from the existing IT platforms. Identify and quantify the quality of existing access rights.
- Reveal the complexities and problems in the current privileges data.
- Build the business case for an IdM project and shape the set of requirements for an RFP.
- Foresee complications and better plan future IdM deployment. Get buy-in from both IT and line of business managers.
- Identify role engineering methodologies that best fit the organization.
- Uncover and demonstrate compliance violations.


- Prepare for the IdM deployment. Plan and evaluate various Identity Management solutions.
- Prioritize systems and project tasks based on urgency and complexities.
- Start cleaning privileges on individual platforms and simplify their structure.


- Deploy an IdM system along with designing a role-based provisioning policy.
- Create and approve an initial set of business roles to be deployed in the provisioning system.
- Collaborate with business managers to define and approve role definitions and privileges assignment.
- Perform initial cleanup on source platform before loading the data into the new IdM system.


- Periodically audit provisioning policies.
- Refine, optimize, and adapt role definitions to business changes.
- Set quality targets and processes to fix privileges exceptions and flawed role definitions.
- Recertify privileges changes and role updates with business managers.
- Automate testing of privileges and roles against business process rules and policies such as segregation of duty. Demonstrate compliance verification.


|