| |
| |
 |
| |
| �We have used Eurekify's Sage to build a few roles for thousands of users. It is clearly an easy method to create roles and maintain them�, Peter Zuenti, Consultant. |
|
|
| |
 |
| |
| �Sage Discovery and Audit provides a quick and easy insight of the authorizations within a company�s infrastructure. Sage helps customers realize the benefits of RBAC�, Koos Jennekens, Senior Consultant. |
|
|
| |
 |
| |
| �Sage provides instrumental tools for managing Roles. With Sage, our customers can very simply and quickly add new Roles or modify current ones according to organizational demands�, Franco Rasello, CEO. |
|
|
| |
 |
| |
| �In order to control user permissions as well as being compliant with regulations, the Identity Management solution alone is not enough. The right way to start with a provisioning solution should be optimizing Roles�, Franco Rasello, CEO. |
|
|
| |
 |
| |
| "In my experience, role-based management is critical for achieving the true benefits and ROI of Identity Management implementation.", Marc Sel, Director - Security Solutions, PwC Belgium. |
|
|
| |
 |
| |
| �We have made incredible leaps forward by applying Eurekify technology to speed up the process aimed at pinpointing user profiles and roles�, Rob Bus, Managing Director. |
|
|
| |
 |
| |
| �Sage is the perfect tool for assessing specific needs within a large organization. It is also important for attaining administrative efficiency, reduce employee downtime and to improve security�, Ophir Zilbiger, CEO, Secoz Ltd. |
|
|
| |
 |
| |
| �Role definition applications can significantly reduce the cost of the process (by 40-60% according to a leading systems integrator). To our knowledge, Eurekify and Beta Systems are the only vendors in this space.�, Michael Tieu and Andrey Glukhov. |
|
|
| |
 |
| |
| �From Years of experience in implementing enterprise user administration systems in large environments, we strongly recommend a structured and business-aligned approach to the implementation method...�, Jesper Oestergaard, CEO. |
|
|
|
|
|
|
 |
| |
|
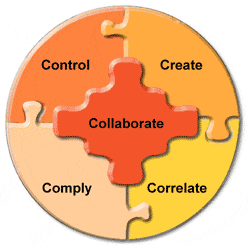
Control, Create, Comply, Correlate, and Collaborate…
 Overview Overview
Many organizations face significant challenges in projects aimed at cleaning up and restructuring privileges in a way that is more manageable and better reflects the underlying business. Privileges cleanup and role-based management are often viewed as pre-requisites to successful implementation of Identity Management systems, and are often required as part of the organizational compliance efforts.
However, many such projects were less than successful because the approach that was taken did not take into consideration significant requirements.
The 5Cs of Role Management
Over the years, Eurekify customers and industry analysts have defined a minimal set of 5 critical requirements that every role-based privileges management system and project must be able to provide.
- Control. In today business and regulatory environment, organizations are required to ensure that users' access is restricted to their needs. Security administrators must always be able to tell who exactly has access to what and why, and to demonstrate that privileges are granted accurately and consistently. Traditionally, however, most organizations have granted privileges in a very ad-hoc way. These privileges were granted to a growing number of employees and external workers, and to an ever growing number of applications. As a result, very few organizations really have control over their privileges, to the point where they can effectively and immediately answer simple questions such as who has access to a resource or a group of resources, what are all the resources someone has access to, who else has access to the resource, how many people have access to a resource, etc. At best, some organizations have some control over some individual platforms.
Eurekify customers, within one week from first installation, gain control over their privileges within and across any number of platforms and applications. They are easily able to answer these and other more sophisticated questions, in a few clicks. With Eurekify, it is also easy to grant privileges consistently and accurately based on a clear role-based policy.

- Create. There is a clear agreement between IT managers, analysts, and software vendors, that the only way to manage privileges effectively is by correlating users privileges to their business roles. Virtually all Identity Management provisioning systems, and indeed any modern enterprise software, support role-based management. However, organizations found it difficult to create an enterprise role-based privileges model that spans across business units, as well as across IT systems. Once constructed, it is also not easy to keep a role-based model synchronized over time with all business changes. Part of the difficulty has to do with the quality of privileges, and part of it is because of the lack of knowledge within the organization. Role engineering also ranks as the number one concern of Identity Management project managers.
Eurekify customers usually create an enterprise role model within a few months, and sometimes within a few weeks. Such a model is quickly defined, easily verified and refined based on analytical comparison to a desired top-down design, as well as against the as-is actual privileges.

- Comply. Organizations wish to ensure that privileges are restricted to the necessary, and that they follow a clear and demonstrable policy. In many cases, organizations no longer have the luxury to proceed at their own pace to enforce such policies. An increasingly growing number of regulations, with an increasingly growing scope, require IT security managers to verify compliance, and often within a very aggressive time frame. Existing systems do not make it easy to verify and enforce compliance across systems and applications. Many organizations have done substantial ground work in this area, but without automation they are likely to have limited and costly success.
Eurekify customers can automate compliance demonstration processes such as Segregation of Duties (SoD) and policy verification, through periodically scheduled batch processes that can be run as often as nightly. Privileges certification and attestation processes can be set up and fulfilled within few days. Business managers are provided with an easy to use web-based facility, enriched with Eurekify's decision support analytics, and providing direct feed into Eurekify's privileges management system.

- Correlate. Organizational privileges are as live as the organization itself. Small and large organizational changes, from the departmental level and up to mergers and acquisitions, must all be reflected in a role-based privileges model. Maintaining a role-based privileges model over time is as challenging as is its initial creation. Without such maintenance, the quality of privileges, and the model itself, are likely to quickly deteriorate to the point where role management will not be able to attain its goals and where a substantial new investment will be required.
Eurekify customers use analytics everywhere to simplify role management processes and ease the efforts. Eurekify continuously correlates privileges; detects inconsistencies and exceptions; detects changes to the business that require changes and adaptations to the model; etc. All stakeholders are provided with analytics-empowered tools to request, adapt, correct, provide feedback, and report on implicit and explicit changes in the privileges, and in the role model itself.

- Collaborate. In privileges management, as in any enterprise undertaking, it is very important to bring together all organizational stakeholders. The creation and adaptation of the overall privileges model can be viewed as a big puzzle, and different people may hold answers to different parts. Privileges certification projects also require substantial collaboration from non-IT business managers. But, in many cases, Identity Management and privileges management projects were unsuccessful at breeding collaboration, and have instead resulted in major tension between IT and the business managers.
Eurekify solutions make it easier for all stakeholders to contribute to the project, and to benefit from it. Business managers are provided with analytics-enhanced web-based solutions that are easy to use and take substantially less time than non-analytic versions – for example, when presented with 1000 privileges to approve, Eurekify also highlights the 30 that seem most out-of-pattern. With Eurekify solutions, business managers no longer fear losing control over their own privileges and those of their team. Instead, they receive all the privileges they need, more accurately, more securely, and in a timely fashion. Internal and external auditors are empowered with the Eurekify solution to more easily specify IT controls; and to have IT automate their enforcement and reporting in a consistent, accurate, and timely fashion. Eurekify solution provides security administrators and role managers with all the tools they need to perform their own job, and to orchestrate the contribution of other stakeholders.

Eurekify Analytical Solutions
Eurekify provides a number of solutions for role-based privileges management and compliance. All Eurekify solutions satisfy the 5Cs. In fact, as the "Rolls Royce" of role-based privileges management Eurekify's solutions add substantial functionality for other privileges management needs as well as numerous luxuries that make management so much more productive and even enjoyable.
The key to Eurekify's solutions success in addressing the 5Cs, as well as in providing other high value-add functionality, is Eurekify's powerful analytics, including its unique and patented use of advanced pattern recognition technology.
In many role management projects, it quickly became apparent that simple automation alone is insufficient to support the more difficult role management tasks. Since 2002, Eurekify started to develop hard-core pattern-recognition analytical technology that will be able to quickly analyze substantial amounts of privileges data, and to provide significant guidance to role managers, auditors, and business managers. Without such analytics it is impossible to quickly and effectively implement role management.
Over the years, Eurekify scientists and engineers have improved this technology, so as to cover additional role management processes, increase time savings and reduce project risks. We remain committed to further improving this technology at the service of our customers. |
According to a recent survey of 150 Identity Management project managers:
 80% plan to implement role-based privileges management as part of their IdM project 80% plan to implement role-based privileges management as part of their IdM project
 75% see role management as the top concern in their IdM deployment 75% see role management as the top concern in their IdM deployment
 More than 50% believe that at least 20% of their privileges are incorrect More than 50% believe that at least 20% of their privileges are incorrect
 81% do not believe that IdM solutions provide adequate tools and methodologies for deploying roles 81% do not believe that IdM solutions provide adequate tools and methodologies for deploying roles
|
|
Why Analytics are So Critical to Effective Role Management
We are often asked whether it is possible to do role management without analytics. In some cases, especially in smaller organizations, it may be possible, but will likely take much more time and frustration. Large organizations have usually discovered that automation alone won't cut it, and that while good methodologies help, they are not sufficient on their own without the support of the right analytical tools.
Lets us try to explain why without sophisticated analytics, many role management processes are very difficult, and may even be infeasible:
- Control. – Without clearly mapping privileges, commonalities, and exceptions, one cannot be sure to gain control, or it takes significantly more time and effort
- Create - Without role mining – the automated discovery of role candidates – role engineering is extremely laborious and error prone
- Comply - Without automated identification of exceptions and violations, one cannot demonstrate compliance
- Correlate - Without automated detection of changing patterns, as well as new inconsistencies, one cannot adapt to business changes, and cannot balance business and security needs
- Collaborate - Without automated detection and highlighting of the most pertinent changes and exceptions, one is not empowering business managers, but merely setting them up with an impossible certification task

|
| |
| |
|
 |